News that discussions among the U.S. government’s top decisions makers about a looming attack on Houthi rebels in Yemen took place on the commercially available Signal messaging app raised a lot of concerns and burning questions. Among these were why was Signal used to talk about such a sensitive matter when there were other more secure, government-provided options available? What were these options and what reasons could possibly exist as to why they were not used? After the news broke, we set out to at least try to get the answer to these questions and more. Here’s what we found out.
Several experts we contacted, including a former acting defense secretary, a retired special operations forces officer and a government secrecy reform advocate, attempted to answer the question of why Signal became the go-to platform for a discussion that included operational details before the mission was launched. Their responses don’t condone the actions, nor do they paint a complete picture of what transpired, because this remains a developing story with a lot of unknowns. However, they offer insights into the technology available to America’s often on-the-go leadership and some perspective on features Signal provides that no government system can — by law.
The actions and the controversy
The mission against the Houthis, launched on March 15, turned out to be successful, according to the Pentagon and the White House. However, the use of Signal, brought to light by The Atlantic after its editor-in-chief Jeffrey Goldberg was somehow added to the group chat called “Houthi PC small group,” sparked widespread concerns about how the Trump administration’s most senior leaders handle sensitive information. The messages included deliberations about whether to attack and when. Later in the text chain, they also featured a play-by-play summary of when the strikes would be launched and by what platforms, which was posted by Secretary of Defense Pete Hegseth. They also mentioned at least one targeted individual.
Beyond these details, the chat, which was setup by National Security Advisor Mike Waltz, also contained several disparaging remarks about allies made by Hegseth and Vice President J.D. Vance. Secretary of State Marco Rubio, CIA Director John Ratcliffe, Director of National Intelligence Tulsi Gabbard and other top leaders were also included in the chat.
The Atlantic revelation spurred several investigations into the matter.
After all, those officials could have used a government desktop terminal in a secure facility to share information over hardened networks like the Joint Worldwide Intelligence Communication System (JWICS) and the Secret Internet Protocol Router (SIPR). Another option could have been a government-issued laptop, tablet or mobile phone designed to access portions of those systems while on the go, depending on the sensitivity of the information. Secure video conferencing is also available in facilities with the proper infrastructure. So why use a messaging app not meant for classified communications and one that the Defense Department (DoD), NSA and Google had issued security alerts about weeks ago, and in the case of the DoD, a day earlier? The NSA warned that even information not categorized as classified should not be shared on Signal, according to a memo obtained by CBS News advising users not to share “unclassified, nonpublic” information on the messaging platform.
While offering relatively secure encrypted end-to-end communications, the Signal app is not approved for the transmission of classified or even sensitive information, nor does it meet the legally required standards for retention of such data.
During previously scheduled congressional hearings about the U.S. intelligence community, Ratcliffe and Gabbard argued that there was no discussion of classified information.
Signal “is a permissible use” application that has been approved by the White House for use by senior officials, Ratcliffe testified, adding that he was given a CIA laptop pre-loaded with the app. The group chat, he acknowledged, was a “mechanism for communicating between senior level officials but not a substitute for using high side or classified communications.” The Pentagon issued a statement on Hegseth’s behalf asserting that there was no exchange of classified information. He made the same argument in an interview, saying he was merely sharing an update.
Several national security experts, however, suggested that by including the timetable, method, means and targets of the attack against the Houthis, Hegseth did inject clearly classified information into the Signal chat.
Even the ODNI’s guidelines seem to back up that contention.
President Donald Trump called the matter “a witch hunt” and said Hegseth “is doing a great job.”
Meanwhile, Democrats accused the administration of lying about the classified nature of information in the chat.
The Atlantic changed its headline from “War Plans” to “Attack Plans” on the follow-up article in which Goldberg provided the full transcript of the chat after Tuesday’s brutal Senate hearing with Gabbard and Ratcliffe. After the additional details were released, it became clearer that the leak did not contain highly detailed war plans as originally insinuated, even though what was being discussed was still of an extremely sensitive nature.
Unclear Signal
The major concerns about Signal are security and records retention. Being end-to-end encrypted, its messages are relatively protected when sent over networks. That level of security is so high that the Swedish military last month urged troops to use it for non-classified messaging “to make it more difficult to intercept calls and messages sent via the telephone network.”
However, should the phone itself be compromised by being lost and unlocked or hit by a certain phishing attack or hack for instance, those messages would be available to unwanted individuals. Just being on Signal enabled Goldberg, a journalist, to inadvertently get access to the chat, one he would otherwise not have been part of on a government system. In addition, using Signal in a public location exposes chat content to anyone trying to sneak a peak if there is a clear line of sight to the device. Moreover, the fact that Signal messages can be set up to disappear forever after a prescribed amount of time makes it wholly unsuitable under federal data retention laws.
Convenience was likely a big factor in the choice to use Signal despite these security risks and prohibitions, several sources told us. It is far easier to whip out a cell phone wherever you are than to have to go into a Sensitive Compartmented Information Facility (SCIF), a secure and electromagnetically hardened room or area used to store, process, and discuss highly classified information. Phones and electronic devices are not even allowed inside. Meanwhile, government-issued mobile devices, as former Biden administration Chief Information Officer Theresa Payton noted, “are difficult to navigate by design.”
Cabinet secretaries should be provided “with integrated, compatible secure [communications systems],” former Acting Defense Secretary Chris Miller, who served at the end of Trump’s first term, told us. “It’s ridiculous. Make the White House [communications office] responsible for issuing and managing. It’s like we are in the 1990s.”
An Army veteran and cybersecurity expert agreed that apps like Signal are faster and easier to use, especially for a chat involving 19 members from numerous agencies.
“The old days of carrying a PC with you everywhere you go, and having an encrypted tunnel and having hardware that protects all that are kind of largely behind us,” said Jared Shepard, who after leaving the Army helped the DoD create a secure network infrastructure in Iraq. He later founded Hypori, a company that provides secure mobile network solutions to several DoD entities. “Now, everybody operates from phones and tablets, and the technology is beginning to catch up.”

“One of the challenges,” he added, “always is how do you successfully share sensitive information across multiple departments. And you know, in the government that is always a challenge.”
“The more secure you make it, the more complex you make it on the user,” Shepard noted. “And so you always have this natural human balance of it has to actually be easy to use, or relatively intuitive to use, if you want users to actually use it. And, from a technology standpoint, if you make it so secure that it’s just too hard to use, then users will find a way around it. It’s just, it’s a human nature thing.”
A government secrecy reform advocate concurred.
“In my experience, dealing with classified records is always a little bit more cumbersome,” explained Lauren Harper, Freedom of the Press Foundation’s first Daniel Ellsberg Chair on Government Secrecy. “I think those systems are probably a little bit less intuitive in terms of how many people were involved.”
A retired special operations forces (SOF) officer questioned the exchange of security for the convenience offered by an app like Signal.
“I went to a number of different countries in support of SOF-type training or for exercises or whatever, and I had a secret or a secure phone,” said the retired SOF officer. “I never had an issue communicating in a timely manner with my secure phone. Now, I wasn’t coordinating national-level strikes or anything, but I’m just saying I don’t know that it’s prudent to sacrifice operational security for maybe a little bit more speed.”
Perhaps a bigger concern than security is that those on the Signal chat may have been trying to avoid records retention.
“I wouldn’t buy the convenience argument as much as I think they were avoiding archiving laws,” Harper told us.
“One of Signal’s key features is that messages disappear,” she explained. “Would Signal be as popular if it didn’t have the disappearing messaging feature? There’s no way to tell.”
“There are also already policies across the government that allow officials to use third-party applications to communicate when they must, provided they forward those records to officials systems within 20 working days,” she added. “A big reason Signal is discouraged as a third-party method is because that’s impossible to guarantee that it is happening when messages can disappear.”
The government watchdog group American Oversight filed a civil lawsuit on Wednesday, alleging that those on the chat violated federal records laws by discussing Houthi attack plans on Signal. In response, a federal judge in Washington on Thursday ordered several Trump administration officials who participated in the Signal chat to preserve all of the messages they exchanged on the app from March 11 to March 15, The New York Times reported Thursday evening.
The government does issue mobile devices designed to handle secure information. In 2017, for example, the Pentagon’s Defense Information Systems Agency (DISA) launched a pilot program expanding its Department of Defense Mobility Classified Capability-Secret (DMCC-S) program to 8-inch tablets, DefenseScoop reported at the time. The objective was to give senior military leaders greater flexibility and the improved user experience they typically would get in the office. The DMCC-S program offers Pentagon officials mobile access to the SIPRNet. Traditionally, the agency issued Samsung Galaxy smartphones to run the DMCC-S program.
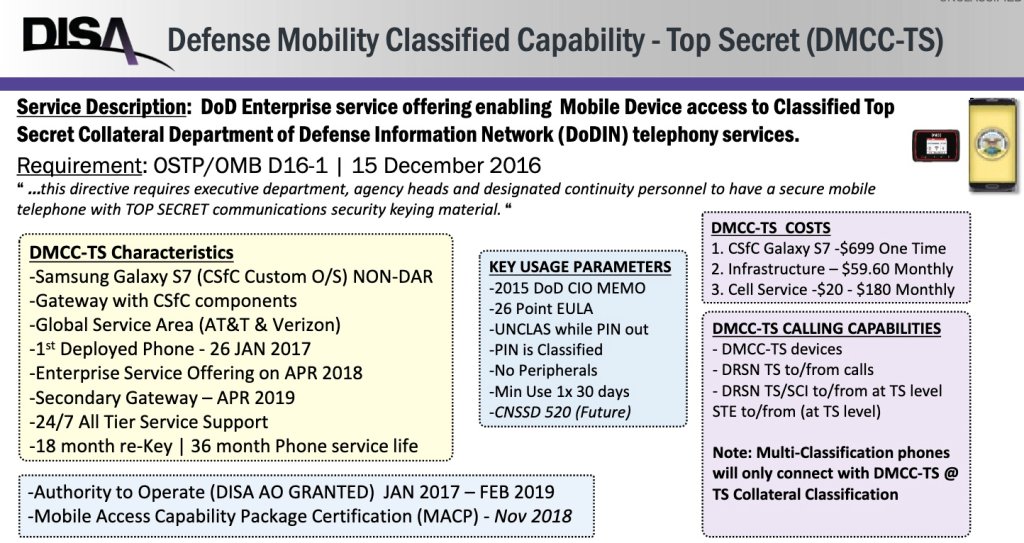
It remains unclear how widely distributed this option has been or whether Hegseth and others on the chat had access to it. DISA declined comment, deferring us to the Pentagon. Officials there have yet to respond to questions about this issue, including whether Hegseth used a government or personal device to access Signal.
We also reached out to the CIA, White House and National Security Council to find out what kinds of devices they issue for secure, mobile communications and which of the cabinet members involved in the chat used personal devices to do so. We will update this story with any pertinent information provided.

Signaling Change
All this begs the question why isn’t there a government-issued app like Signal, especially if it’s being used by those handling sensitive information anyway?
“The government could develop a secure app or incorporate Signal and its use on secure mediums however, Signal is open source and independently audited,” the retired SOF officer posited. “This may raise suspicion about backdoors or surveillance of government employees raising concerns among stakeholders. Also, since Signal is a commercial app right now and commercial apps usually update frequently in order to better the user experience and incorporate security patches, the government tends to be slow and bureaucratic in incorporating these changes.”
Harper suggested that the question about why there is no government-issued app like Signal “is hard to directly answer because it also depends on agency rules around handling classified information.”
“You can’t separate the two issues of convenience and secrecy when trying to discuss whether or not the government should have applications like [Signal],” she suggested.
“It’s not just a question of what technical capabilities an agency may have,” she added, “but how it comports with classification guidelines that have to be improved by the Information Security Oversight Office and in compliance with the executive order on classified national security information, 13526,” issued in 2019 under then-President Barack Obama.

Shepard, the Hypori CEO, said his company provides a secure mobile communications system being used by the U.S. Army, U.S. Air Force, U.S. Special Operations Command, U.S. Space Force and DISA.
“We meet the right guidance under the NSA,” he said. “We do have the ability to do classified communications in a mobile environment” on government-issued devices.
“Could the members of that Signal chat have had a classified version of Hypori instead and then done everything within the requirements to have a classified conversation?” he asked rhetorically. “The answer is yes, they could have done that.”
Even if the Signal controversy now consuming Washington blows over as newer issues come to the forefront, the underlying issues will remain. The need for highly secure, mobile and easy-to-use communications that retains its messages for those handling sensitive matters will only increase as the world moves faster with each passing day. And apparently, some in the highest reaches of power have moved ahead with the convenience an app like Signal provides, whether the government’s security apparatus likes it or not.
Contact the author: howard@thewarzone.com
