Russia’s Rubin Design Bureau was the target of a cyber attack involving an image file with malicious software embedded inside it via a specific tool that has become a hallmark of multiple entities linked to the Chinese government. The file could have been used to create a backdoor into the networks at Rubin, a prolific designer of submarines and other underwater platforms. Its portfolio includes the ultra-quiet Borei class ballistic missile submarine, the unique Belgorod and Losharik special missions submarines, and the Poseidon nuclear-powered and nuclear-armed ultra-long-range ‘doomsday’ torpedo, among other work.
Cybersecurity firm Cybereason first reported on the attack on April 30, 2021, but it’s unclear when it was actually carried out. Metadata that the company provided along with its analysis says that the Rich Text Format (RTF) image in question was created in 2007, but the report says that this is almost certainly false and meant to help obfuscate its origins. Other portions of the metadata indicate that it was first accessed earlier in April, but that may just be when Cybereason first opened it up to assess it. It’s also not clear if the attack was successful in any way.

“The initial infection vector is a spear-phishing email addressed to the “respectful general director Igor Vladimirovich [Vilnit]” at the Rubin Design Bureau, a submarine design center from the ‘Gidropribor‘ concern in St. Petersburg, a national research center that designs underwater weapons like submarines,” Cybereason’s report says. “The email attachment is a malicious RTF document weaponized with a RoyalRoad payload, with content describing a general view of an autonomous underwater vehicle.”
A “spear-phishing” attack involves tricking an individual into opening a file, received via Email or some other source, that contains malicious software (malware). That malware then infects the target’s computer, and potentially other parts of any networks it is linked to, either carrying out certain malign tasks directly or providing a vector through which additional attacks can be carried out.

In this case, according to Cybereason, the attackers used a program called RoyalRoad to embed a separate file, winlog.wll, into the RTF image. That subfile would then have loaded a piece of malware, called Portdoor, onto the target computer when the TRF was opened.
Cybereason said that Portdoor was “a previously undocumented backdoor” and had “the ability to do reconnaissance, target profiling, delivery of additional payloads, privilege escalation, process manipulation static detection antivirus evasion, one-byte XOR encryption, AES-encrypted data exfiltration and more.” In short, it could have identified files of interest on the target computer, and potentially on networks it was linked to, and then paved the way for further attacks to either steal that information or carry out other malicious tasks.
The individuals who launched the cyber attack on Rubin are not identified in this report, which only says that the “previously undocumented backdoor [was] assessed to have been developed by a threat actor likely operating on behalf of Chinese state-sponsored interests. Beyond that, the RoyalRoad RTF “weaponizer” is a tool that has become very closely associated with Chinese government-linked entities, known by names like Goblin Panda, Rancor Group, TA428, Tick, and Tonto Team, according to Cybereason and other sources.
The Chinese government is certainly well-known for engaging in industrial espionage, including via cyberattacks, against foreign companies to steal information about military and non-military projects, as well as systems that could have both military and civilian applications. However, public reports about such incidents more typically involve Western companies or major firms in East Asia, rather than those in Russia.
The attack on Rubin is particularly notable given China’s efforts to expand the overall size and capabilities of its submarine fleets, especially with the introduction of new, quieter, nuclear-powered ballistic and guided missile submarines. Though Russia’s own defense acquisition and modernization efforts are often limited by budgetary issues and other factors, the country still has a significant knowledge base when it comes to the development of advanced submarines, thanks to Rubin, as well as the Malakhit Design Bureau. That latter firm developed the Yasen and Yasen-M class super-quiet guided-missile submarines. The Russian Navy just recently received its first Yasen-M, the Kazan, and you can read more about both types here. Rubin’s website says that it, alone, has been responsible for the development of 85 percent of Soviet and Russian Navy submarines since 1901.

As already noted, Rubin has also been responsible for the development of a number of novel and otherwise highly specialized underwater systems, another area that China is increasingly interested in, as well. The Russian company’s design work in this field includes the Poseidon torpedo, seen in the video below, and the Harpsichord large unmanned underwater vehicle (UUV), also intended for deployment from manned submarines.

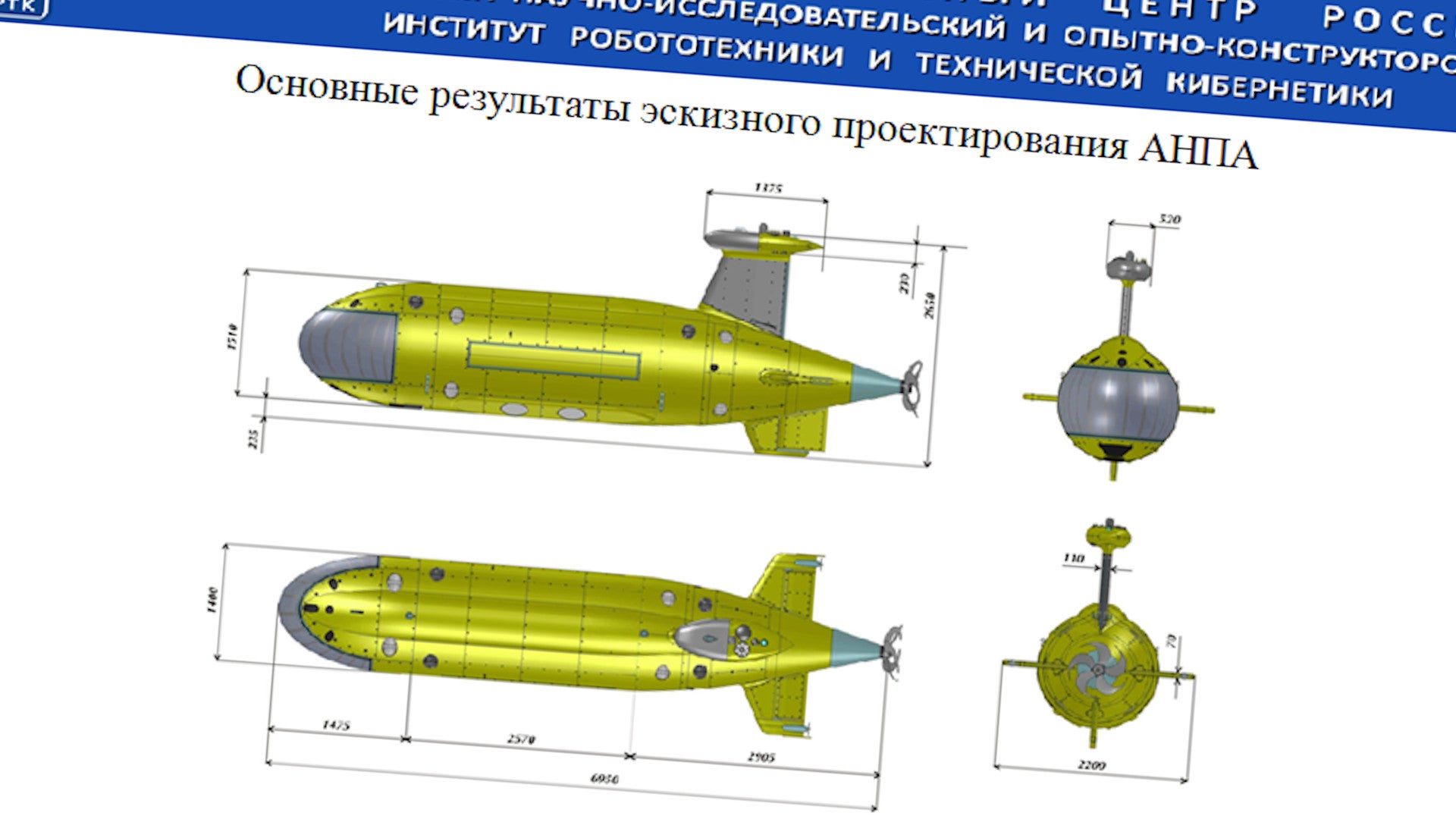
It has also been developing another relatively large UUV, known as Cephalopod, which could potentially operate as a fully autonomous armed mini-submarine. Interestingly, the image in the spear-phishing Email sent to Rubin’s director was a graphic of a design that appears to be at least closely related to Cephalopod.


It’s not clear where the attackers might have initially obtained that image or if they faked it themselves. “Whoever drew it knew a lot about AUVs and Rubin designs. So the image itself appears legit,” H.I. Sutton, an expert on all things that operate underneath the waves, wrote regarding this entire report on his website, Covert Shores. Either way, whoever was behind the cyber attack could have used the graphic to further try to fool Vilnit into thinking it was an internal message and get him to open it.
It’s also interesting to remember that a report emerged last year that Beijing and Moscow were cooperating on the development of a new non-nuclear submarine design. The Chinese People’s Liberation Army Navy (PLAN) already operates two Russian-made Kilo class diesel-electric attack submarines, as well as 10 more so-called Improved Kilos with enhanced performance and sonar capabilities, both of which are also Rubin designs. At the same time, there have been suggestions that this partnership could benefit Russia more than China since the latter appears now to be leading the two in the development of air-independent propulsion (AIP) systems used in very quiet diesel-electric designs.

Regardless, there are many instances where China has cooperated with foreign firms, including those in Russia, on the development, as well as production, of certain military systems, only for Chinese concerns to subsequently begin making unlicensed clones and derivatives. The Kremlin itself has publicly said that it has engaged with its counterparts in Beijing in the past on this matter, generally, as a potential impediment to future Russian arms sales to China.
“Unauthorized copying of our equipment abroad is a huge problem. There have been 500 such cases over the past 17 years,” Yevgeny Livadny, the Chief of Intellectual Property Projects at Rostec, Russia’s main state-owned industrial conglomerate, said in December 2019. “China alone has copied aircraft engines, Sukhoi planes, deck jets, air defense systems, portable air defense missiles, and analogs of the Pantsir medium-range surface-to-air systems.”
No matter what, if the cyber attack on Rubin was indeed Chinese state-sponsored, it would certainly seem to indicate that officials in Beijing feel that there is much to be gleaned from that design bureau’s work to further its own underwater ambitions. How this incident might impact further Russian-Chinese cooperation on submarines, or any other major industrial projects, defense-related or not, remains to be seen.
Contact the author: joe@thedrive.com