If there’s one place one can find plenty of nicknames, it’s within the sprawling landscape of the armed forces. When it comes to the greater civilian world, there’s no historical precedent or agreed upon social norm for how someone or something gains a substitute informal title. However, given the Department of Defense’s fondness of rigid structure, it should be no surprise that when it comes to nicknames, there’s a policy for them, too.
Meet NICKA
Prior to 1975, names for military operations and projects were exclusively chosen at the behest of military commanders. As a result, within the annals of American military history one can find a diverse range of interesting titles from Operation Killer—a major 1951 counter-offensive during the Korean War—to Operation Beaver Cage—a U.S. Marine Corps operation that occurred during the spring of 1967 as part of the Vietnam War.
However, shortly after the close of the Vietnam War, the Joint Chiefs of Staff (JCS) decided it was time to formalize the use of code words and nicknames by unveiling the Code Word Nickname and Exercise Term System, colloquially known as NICKA.
For the Department of Defense (DoD), NICKA is both a set of policies governing the selection of defense monikers and a military-wide computer system that archives and prevents duplication of terms.
Important to note, NICKA is primarily used for Department of Defense-related endeavors. Many operations or programs emerging from within the intelligence community use their own separate naming system.
For example, the Central Intelligence Agency uses the Cryptonym system for developing code words and names. It is also worth noting that the National Security Agency (NSA), National Geospatial-Intelligence Agency (NGA), Defense Intelligence Agency (DIA), and National Reconnaissance Office (NRO) all use the NICKA system
NICKA outlines three distinctive types of monikers that can be used within the DoD:
- Code Words
- Nicknames
- Exercise Terms

Code Words
In NICKA, a code word is a single word that’s assigned to any program or operational plan that’s classified confidential or higher. Each component agency in the Department of Defense are assigned blocks of code words by the Joint Staff. When needed, the NICKA computer program will randomly select and assign a code word from the originating agency’s allocated block of terms.
For example, in the lead up to the Gulf War, when the Combat Aviation Brigade of the 1st Armored Division needed a code word for their forward assembly area, the NICKA computer system pulled from one of the Army’s predetermined block designations and selected the amusingly mundane code word—LARRY.
Essentially a password for entry in an exclusive club, the preeminent role of code words is to restrict access to sensitive national security information to only those who have a need to know. Assisting security, a code word itself will be safeguarded by being classified by one of the three security classifications—confidential, secret, or top secret—based on the security level of the associated program.
Virtually anything conceivably classified, including programs, projects, locations, operations, objectives, missions, or plans, can be assigned a code word. One particular area code words can be highly prevalent is with Special Access Programs (SAP). As mentioned in The War Zone’s in-depth look at Special Access Programs, multiple components, sub-components, and projects can sprawl out from a single SAP “umbrella.” In this compartmentalized system of security, each of the different appendages of one SAP can potentially be assigned their own specific code word.
Once NICKA assigns a code word, it’s considered active. An active code word will remain unchanged for the life of a program and cannot be altered by its users. The one exception being if there’s a concern a code word had been compromised. In this instance, a new code word would be issued. Equally, in certain situations, an unclassified cover term may get applied to a program for counterintelligence purposes.
In addition to the obvious security and oversight reasons, the principal reason for a code word’s permanence relates to the significant role NICKA serves as an archive of all active and inactive code words. The system uses its database of terms to prevent any potential conflicts that could arise due to similarities or duplication of previous code words.
As a Department of Defense system, NICKA will only assign single-word code words. However, in some instances, the Pentagon may take over a project or program that originated outside of the DoD, such as from the Central Intelligence Agency (CIA), Department of Energy (DOE), commercial companies, or even foreign governments. In these instances, already assigned code words may not follow NICKA guidelines. In these occurrences, a program may be reassigned a new NICKA code word or the previous unregulated code name may be maintained.
Regardless, of whether it’s kept or not, the non-NICKA code name may still be added to the program’s database to stem off any future confusion or conflict.
For example, technically before NICKA’s time and not a DoD project, the 1960s A-12 reconnaissance plane was developed and operated under the CIA code word “OXCART”. However, Kelly Johnson and his pioneering team of engineers at Lockheed Skunk Works used the code word “ARCHANGEL” for the A-12. Furthering the spy plane’s eventual identity crisis, flight crews would nickname the A-12 “Cygnus.”
Though OXCART was the only officially assigned government code word, under NICKA, both the contract code word, “ARCHANGEL” and the A-12’s nickname “Cygnus,” would equally be archived to prevent duplicate use.
When it comes to code words. Many real-world military operations and programs, for example, “HAVE BLUE,“ “ACID GAMBIT,” “AUTUMN RETURN,” “SENIOR TREND,” or the infamous “YELLOW FRUIT,” are often reported as being the “code word” for a classified operation or program. However, per DoD and the Joint Chiefs NICKA policy, a code word always consist of just a single word. By NICKA, the above named examples would be “nicknames” and not code words.
This does not mean that multiple code words cannot apply to a certain entity. Any intelligence product that contains Top-Secret NATO information would carry the code word “COSMIC” in addition to any other applicable ones. Certain categories of sensitive activities can even involve code words that become intrinsically linked and enter common usage linked together. “TALENT,” an overarching code word for aerial intelligence-gathering assets, such as the U-2 Dragon Lady and SR-71 Blackbird spy planes, and “KEYHOLE,” which covers intelligence-gathering satellites, are no longer treated as separate from each other officially and one will routinely see documents marked “TALENT KEYHOLE,” or using the abbreviation “TK,” as a single term.
Nicknames
As we briefly mentioned, when it comes to the designation of nicknames, NICKA offers some flexibility and gives military commanders the ability to be a little more creative.
Whereas NICKA only assigns single-word code words, by policy, nicknames must be comprised of two separate words. Similar to the code word process, each DoD component agency is assigned a set of designated numerical block assignments by NICKA. In turn, the agency’s numerical block assignment will correspond to “alphabetical assignment list,” which is a range of two-letter alphabetical sets. The first word of any nickname must come from within an agency’s assigned alphabetical range.
For example, using the now obsolete and unclassified NICKA block assignments, if a program within the Defense Intelligence Agency (DIA) needed to come up with a nickname, one would start by identifying the four numerical blocks assigned to the DIA (15, 33, 51, and 76).

The next step would be identifying what ranges of two-letter combinations would be associated with an agency’s assigned blocks. Following along with the previous example, based on the alphabetical assignment list, the first word of a DIA program nickname would have to start with:
Block 15 – Letters DM – DR
Block 33 – Letters IA – IF
Block 51 – Letters MM-MR
Block 76 – Letters SS – SZ
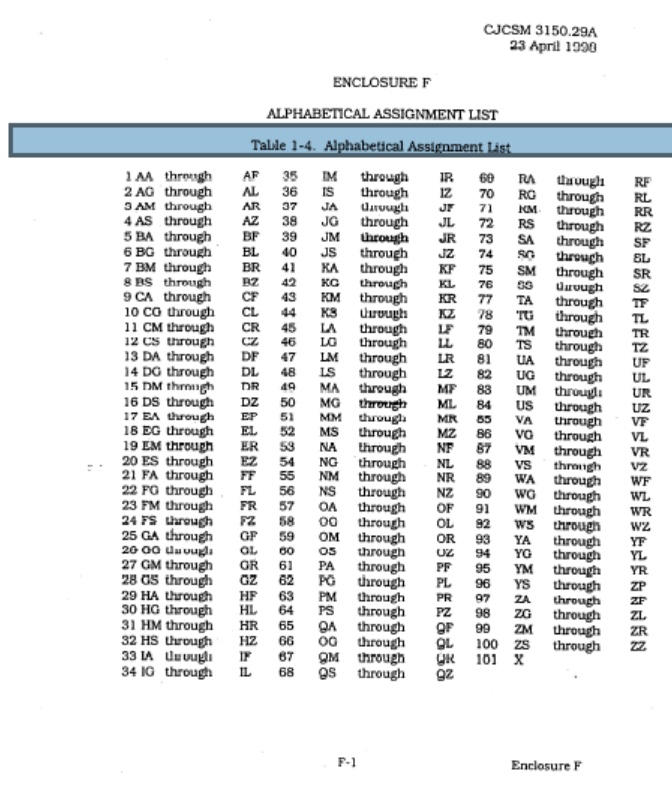
Once the alphabetical block assignments are determined, for military commanders, the process then becomes a word-search of sorts in order to come up with an appropriate first word for a nickname that fits within the designated letter combinations. In our example, the words “DOOM,” “IDEAL,” “MOON,” or “STEREO” would all fit the criteria as being acceptable first words for a DIA nickname.
Below is a more specific set of examples straight from the U.S. Central Command’s (CENTCOM) regulation regarding NICKA:

When it comes to the second portion of the two-word requirement for nicknames, military planners have the unrestricted ability to get creative, provided phrases are not “improper” or “counterproductive.”
By NICKA guidelines, improper nicknames would be terms that are:
- Inconsistent with traditional American ideals or current foreign policy.
- Offensive to good taste or derogatory to a particular group, sect, or creed.
- Offensive to U.S. allies or other free world nations.
Additionally, NICKA forbids nicknames from being:
- Any two-word combination voice call sign found in the Joint Army Navy Air Force Publication Call Sign Book (JANAP-119).
- Include the words, “Project, Exercise, or Operation.”
- Words that may be used correctly either as a single word or as two words, such as “moonlight.”
- Exotic words, trite expressions or well-known commercial trademarks.
By military standards—where one can often find rules for rules—NICKA guidelines on nicknames are fairly limited and debatably common sense. Thanks to the tempered flexibility NICKA gives to nicknames, the system still affords for some bellicose poetry like “Beast Master”—a 2006 Army operation to clear the Baghdad suburb of Ghazaliya—an area itself (unofficially) nicknamed “IED Alley East,” or “Viking Snatch”—a 2007 counterinsurgency operation in Iraq. Still, especially at lower levels of command and for short-duration operations, one still often sees nicknames that do not comply with NICKA, including ones with single words.

In contrast to code words, nicknames, including their descriptions, meanings, and relationship, are also, by policy, supposed to remain unclassified, though the branches of the U.S. military still routinely classify them on the ground of national security. In addition, NICKA guidelines stipulate nicknames are not required, but can be assigned to actual real-world events, projects, or activities. One caveat to “not required” being with Special Access Programs, which are required to have an unclassified nickname assigned to them.
Exercise Terms
Rounding out NICKA’s trifecta of officially sanctioned phrases, are exercise terms. As the name implies, exercise terms are monikers assigned to tests, drills, or exercises, which are assigned for the purpose of emphasizing the event is not an actual real-world operation. That said, the military has a bad habit of not sticking to DoD rules when it comes to publicizing or describing training exercises, often describing them as “operations.”
For example, “Llama Fury” was a week-long Explosive Ordnance Disposal (EOD) training exercise at Seymour Johnson Air Force Base in late summer of 2015. By NICKA policies, Llama Fury should have carried the “exercise” moniker. However, in press releases, multiple Air Force Public Affairs Offices described the event as “Operation Llama Fury.”
Though technically their own classification, exercise terms are more or less an extension of NICKA nicknames, with their selection and regulation falling under the same agency assigned alphabetical block system as the nicknaming process.
Since some military training evolutions are regularly repeated, certain specific exercises will carry the same name with an added numerical postfix indicating the month or year the event occurs. For example, held annually from 2006 to 2018, some of the largest U.S. military war games ever performed in the Pacific Ocean were all conducted under the exercise term “Valiant Shield.” Since this training event was repeated for twelve-years, a four-digit identifier for the year training maneuvers were performed would accompany the exercise term, producing “Exercise Valiant Shield 2017,” and so on and so forth.

For exercises that occur multiple times in a fiscal year, like “Swift Response,” a large training event between the U.S. and its European allies, the second iteration of the exercise in 2017 would be called “Swift Response 17-2.”
Least ambiguous of NICKA’s trio, code words play an essential role safeguarding extremely sensitive secrets. However, when it comes to nicknames and exercise terms, this aspect of NICKA is arguably more significant.
For example, “Enduring Freedom,” (the U.S. Global War on Terrorism, though often applied solely to operations in Afghanistan), “Iraqi Freedom,” (the 2003 invasion of Iraq and subsequent occupation), or “Inherent Resolve,” (the U.S. military intervention in Iraq and Syria to combat ISIS), are not merely nicknames, these phrases are meant to inspire and express the overarching intent of military involvement.
More than just iconic inscriptions on military ribbons, medals, and service records, the perceptions associated with a few major military nicknames or terms become ingrained in the public’s collective conscious and often end up being enduring aspects of American history.
So, there you have it. All those cool-sounding program nicknames, secretive code words, and intense sounding military exercises you probably heard of over the years, all likely came from a highly structured, yet obscure Department of Defense system puzzlingly named NICKA.
Contact the editor: Tyler@thedrive.com
